Protecting Web Servers from Distributed Denial of Service Attacks(DDoS):
Possible SYN flooding on port 80. Sending cookies:
If frequently faced an outage of web services. On investigating, I found that it had something creeping up in it's logs. Something which read -
kernel: possible SYN flooding on port 80. Sending cookies.
It looked like a Denial of service attack. It was evident that I needed to beef up security!
Avoiding a DDOS attack on a web server:
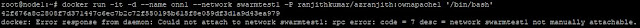
iptables comes with a module (limit) using which a DDOS attack can be tackled. Depending on the type of web service running on the server, I decided a limit of 15 HTTP syn packets per second would be enough.
First, We had a look at the existing rules
# iptables -L -v
This shows you the rules and the default policy that are set in the existing chains - INPUT, FORWARD and OUTPUT.
Then we followed these quick steps -
1. Create a new chain and name it, say, DDOS_SYNFLOOD,
# iptables -N DDOS_SYNFLOOD
2. Add a limit to no.of packets 15 per second with a max burst of about 20, by using the limit module.
# iptables -A DDOS_SYNFLOOD -m limit --limit 15/second --limit-burst 20 -j ACCEPT
Note: Other units - /minute , /hour , and /day
3. And of course, we will need to drop packets which exceed the above limitation
# iptables -A DDOS_SYNFLOOD -j DROP
4. Now all that was left was to "jump" to this new chain for incoming tcp syn packets on port 80.
# iptables -A INPUT -p tcp --syn --dport http -j DDOS_SYNFLOOD
And to look at what was set up -
# iptables -L -v
Chain INPUT (policy ACCEPT 95 packets, 4988 bytes)
pkts bytes target prot opt in out source destination
0 0 DDOS_SYNFLOOD tcp -- any any anywhere anywhere tcp dpt:http flags:FIN,SYN,RST,ACK/SYN
......
......
......
......
Chain DDOS_SYNFLOOD (1 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- any any anywhere anywhere limit: avg 15/sec burst 20
0 0 DROP all -- any any anywhere anywhere
And since then, We have had a few peaceful nights.
We should remember, iptables works sequentially and jumps to the target of the first match. Hence, you will need to ensure that there are no conflicting rules ahead of this one to avoid an undesired result.
I also added,
# echo 1 > /proc/sys/net/ipv4/tcp_syncookies
More info on limit module:
limit
This module matches at a limited rate using a token bucket filter. A
rule using this extension will match until this limit is reached
(unless the `!' flag is used). It can be used in combination with the
LOG target to give limited logging, for example.
[!] --limit rate[/second|/minute|/hour|/day]
Maximum average matching rate: specified as a number, with an
optional `/second', `/minute', `/hour', or `/day' suffix; the
default is 3/hour.
--limit-burst number
Maximum initial number of packets to match: this number gets
recharged by one every time the limit specified above is not
reached, up to this number; the default is 5.
Relish !!!
If frequently faced an outage of web services. On investigating, I found that it had something creeping up in it's logs. Something which read -
kernel: possible SYN flooding on port 80. Sending cookies.
It looked like a Denial of service attack. It was evident that I needed to beef up security!
Avoiding a DDOS attack on a web server:
iptables comes with a module (limit) using which a DDOS attack can be tackled. Depending on the type of web service running on the server, I decided a limit of 15 HTTP syn packets per second would be enough.
First, We had a look at the existing rules
# iptables -L -v
This shows you the rules and the default policy that are set in the existing chains - INPUT, FORWARD and OUTPUT.
Then we followed these quick steps -
1. Create a new chain and name it, say, DDOS_SYNFLOOD,
# iptables -N DDOS_SYNFLOOD
2. Add a limit to no.of packets 15 per second with a max burst of about 20, by using the limit module.
# iptables -A DDOS_SYNFLOOD -m limit --limit 15/second --limit-burst 20 -j ACCEPT
Note: Other units - /minute , /hour , and /day
3. And of course, we will need to drop packets which exceed the above limitation
# iptables -A DDOS_SYNFLOOD -j DROP
4. Now all that was left was to "jump" to this new chain for incoming tcp syn packets on port 80.
# iptables -A INPUT -p tcp --syn --dport http -j DDOS_SYNFLOOD
And to look at what was set up -
# iptables -L -v
Chain INPUT (policy ACCEPT 95 packets, 4988 bytes)
pkts bytes target prot opt in out source destination
0 0 DDOS_SYNFLOOD tcp -- any any anywhere anywhere tcp dpt:http flags:FIN,SYN,RST,ACK/SYN
......
......
......
......
Chain DDOS_SYNFLOOD (1 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- any any anywhere anywhere limit: avg 15/sec burst 20
0 0 DROP all -- any any anywhere anywhere
And since then, We have had a few peaceful nights.
We should remember, iptables works sequentially and jumps to the target of the first match. Hence, you will need to ensure that there are no conflicting rules ahead of this one to avoid an undesired result.
I also added,
# echo 1 > /proc/sys/net/ipv4/tcp_syncookies
More info on limit module:
limit
This module matches at a limited rate using a token bucket filter. A
rule using this extension will match until this limit is reached
(unless the `!' flag is used). It can be used in combination with the
LOG target to give limited logging, for example.
[!] --limit rate[/second|/minute|/hour|/day]
Maximum average matching rate: specified as a number, with an
optional `/second', `/minute', `/hour', or `/day' suffix; the
default is 3/hour.
--limit-burst number
Maximum initial number of packets to match: this number gets
recharged by one every time the limit specified above is not
reached, up to this number; the default is 5.
Relish !!!
Comments
Post a Comment